Governance, Risk Management and Compliance
The software solution that helps you comply with security frameworks
- It allows you to define and develop, with a documentary and systematic approach, an adequate Information Security Management.
- It helps you ensure that acceptable risks do not become obstacles to achieving your business objectives.
Improve your security strategy, reduce risks, and ensure compliance
We define and develop strategies and structures to keep your organization safe
- We are experts in the implementation of ISO 27001 and ENS
- We know how to define the Security Master Plan that your company needs.
- We ensure compliance with GDPR and LOPDGDD.
Security Consulting
Services
We define and prioritize a set of information security projects aimed at reducing the risks to which the organization is exposed to acceptable levels, based on an analysis of the initial situation.
It is essential that an SMP:
- Aligns with the company’s strategic objectives.
- Includes a definition of scope.
- Incorporates the security obligations and best practices that workers of the organization, as well as third parties collaborating with it, must comply with.
The main benefits of carrying out an SMP are:
- Identifying the areas most exposed to potential attacks or security breaches.
- Understanding and implementing actions that help reduce risks.
- Having contingency measures and plans in place beforehand.
- Establishing internal regulations to govern security.
This international standard provides a framework for Information Security Management Systems, aiming to ensure the confidentiality, integrity, and continuous availability of information, as well as legal compliance.
Obtaining accredited ISO 27001 certification demonstrates that your company is committed to following information security best practices.
The benefits of implementing ISO 27001 are:
- Greater competitive advantage.
- Identification and reduction of risks.
- Legal compliance.
- Increased trust and improved brand image.
- Periodic reviews.
- Cost reduction.
JakinCode supports you in the process of adaptation and implementation to the ENS. The ENS is a legal standard with mandatory requirements and ongoing management demands, aimed at ensuring that the digital information systems of Public Administrations, as well as the companies and professionals who provide services to them, achieve the necessary security.
Its objective is to guarantee the security of computer systems by providing protection for the information they handle and the services offered by the Public Sector, enabling secure and reliable digital interactions.
Our consultancy specializes in training and guiding our clients to comply with data protection laws in their organizations. We offer expert and practical advice to ensure compliance with current privacy regulations, including the General Data Protection Regulation (GDPR) and its adaptation to the Spanish legal framework through the Ley Orgánica de Protección de Datos y Garantía de Derechos Digitales (LOPDGDD).
Take advantage of the benefits of no longer manually handling the implementation of Security Management Systems in your organization:
Facilitates regulatory compliance
Ensures working with the best practices
Helps in adapting to a ever-changing context
Automates risk análisis
JakinSuma makes it easy for you to comply with the following security frameworks:
ISO 27701
ENS – National Security Framework
ISO 27001
ISO27017
ISO 27018
GDPR
DORA
NIS2
TISAX
 add
add
add
add
add
add
add
add
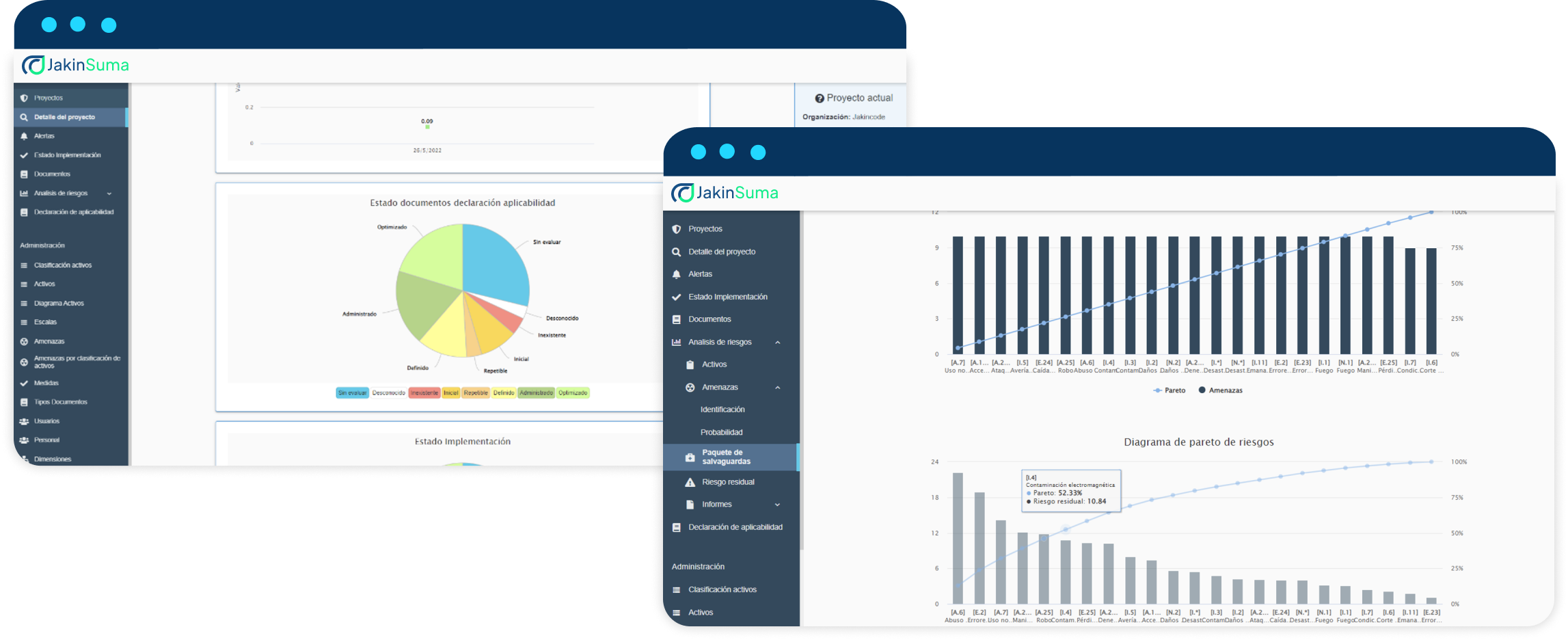
Dashboard
Through a detailed dashboard, it allows us to know the status and degree of compliance.
Document Manager
It facilitates the control of all documentation in an orderly and accessible manner.
Analysis and Risk Management
It enables a risk analysis adaptable to any methodology with an evaluation of the risks through diagrams or reports.
Continued compliance
It allows ongoing adaptation with a comparison between periods.
Other regulations of your interest
We assist you in obtaining certification for compliance with best practices regarding Personal Data Management, which your organization must protect.
This standard outlines the necessary requirements and provides clear guidelines for establishing, implementing, maintaining, and continuously improving an Information Management System for Personal Data Protection (PIMS) through security controls. It enhances accountability in data handling and the security of personally identifiable information.
ISO 27701 is considered an extension of ISO 27001 and ISO 27002 standards, enabling the development and enhancement of processes for managing personal information within any organization, supporting compliance with GDPR and other data privacy requirements.
These two standards are intended for Information Security Management Systems in Cloud Services. ISO 27017 refers to security controls that serve business processes in the cloud, and ISO 27018 extends management systems to include the protection of personal information stored in the cloud.
This standard allows taking measures to manage the risks to which an organization’s Business Continuity is exposed.
The main benefits of integrating this standard are:
- Minimizing the consequences of a potential disruption of business activities.
- Ability to prevent or avoid the effects of an incident.
- Greater flexibility in the face of activity interruptions.
- Reducing costs related to interruptions.
- Having a structured methodology to resume activities after an interruption.
Through a Strategic and Global Risk Management approach, we work to turn risk into opportunity.
The guidelines and recommendations set forth in the standard are aimed at corporate risks, enabling progress in managing other more specific types of risks such as operational, financial, or strategic risks.
The scope of these standards is the Security of Industrial Automation and Control Systems (IACS). Seeking to address the threats associated with them, the main objective is to facilitate the handling of vulnerabilities of IACS against cyber-attacks and the implementation of measures to mitigate them.
Our experts are at your disposal
Shall we schedule a meeting?
The opportune moment to meet and talk
about how we can provide solutions
to your cybersecurity.